This section shows the DoS protection rules available and allows to edit them. Keep in mind that every change in this section has to be applied clicking on the Update button.
Global Settings DoS Rules
The Global Settings for every type of DoS rule depends on the type of the rule itself. See below the different options.
- Name. By default the name of the DoS rule.
- Type. The type of the rule, either System or Farm.
- Rule. Which kind of rule of all defined ones, the current kind of Dos Protections are:
- Connection limit per second.
- Total Connections limit per source IP
- Check bogus TCP flags
- Limit RST request per second
SSH Brute Force
In addition to the previous four farms rules there is a system rule called ssh_brute_force. It is already preloaded and can not be deleted. If enabled it protects the system against the SSH password bruteforce attacks. Thus it can not be applied to a given farm. Instead it only can be applied to the entire system.
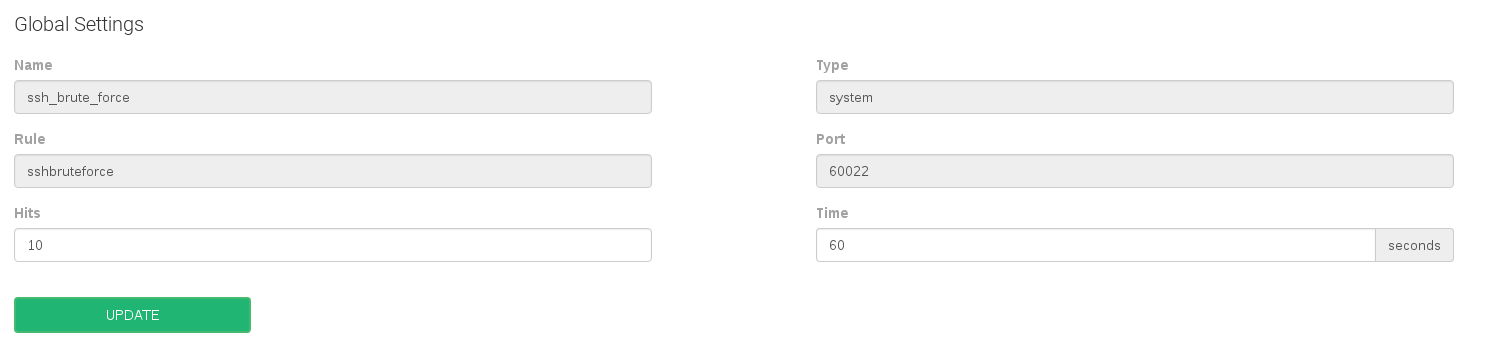
Some settings in regards to the SSH brute force rule are:
- Port. It can’t be changed and it’ll be gathered from the SSH service configuration.
- Hits. Number of incorrect logins attempts before blocking an IP source address.
- Time. Seconds that a certain IP address will be blocked if the number of hits is reached.
Connection limit per second
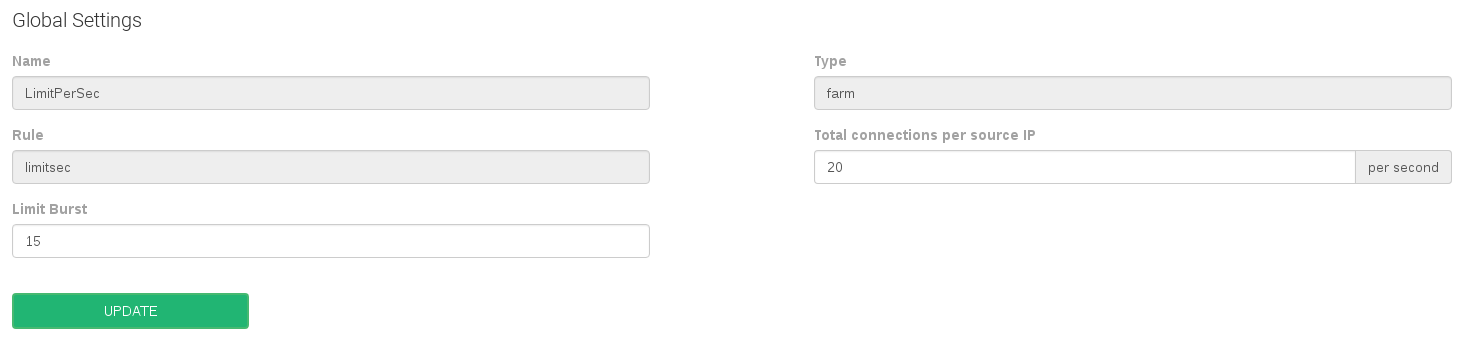
Some settings in regards to the connection limit per second rule are:
- Total connections per source IP. Number of connections allowed in a certain time slot per client or source IP address. This option acts like a soft limit.
- Limit Burst. Number of allowed connections per source IP address before the limit of 1 per second blocking. This option acts like a hard limit.
Total connections limit per source IP
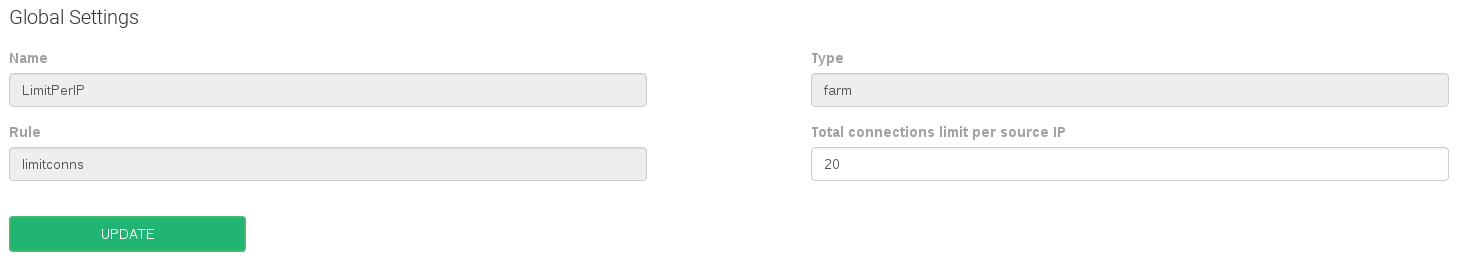
- Total connections limit per source IP. Number of total connections allowed per client or source IP address.
Check bogus TCP flags
No global settings available for this rule.
Limit RST request per second
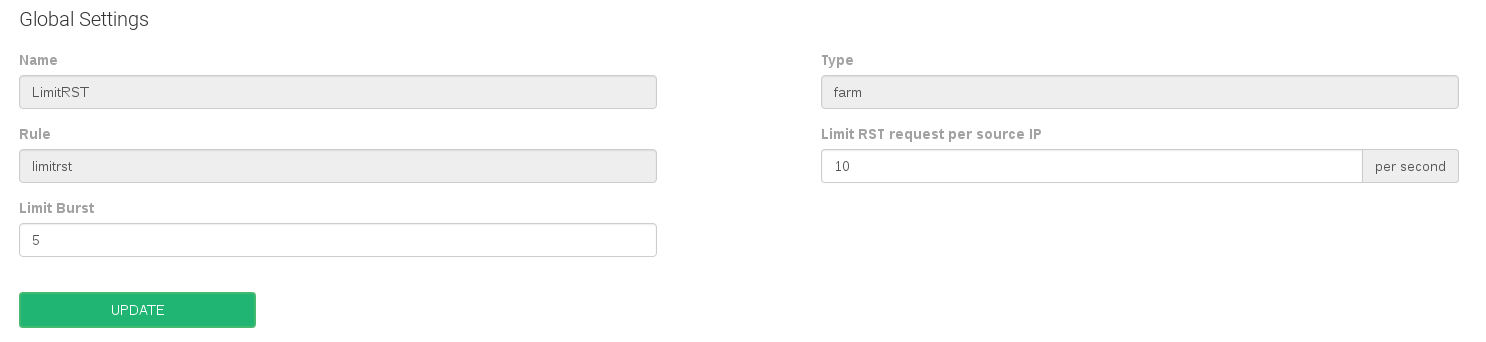
- Limit RST request per source IP. Number of RST packets allowed per client or source IP address. This option acts like a soft limit.
- Limit Burst. Number of allowed RST packets per source IP address before the limit of 1 per second blocking. This option acts like a hard limit.
Farms DoS Rules Settings
This section allows to assign farms to the DoS rules defined, through the Farms tab when updating a rule.
The available actions in this section are:
- Add Farm. Add a new farm service in a given DoS rule. When assigning a new farm, a combo list of all the configured farms will be shown, either they’re running or not.
- Unset. Deallocate a farm service to a certain DoS rule and stop applying the rule to a given farm service.
The unset action is applied one by one, or by a group of farms services through the multiple selector.

Comments